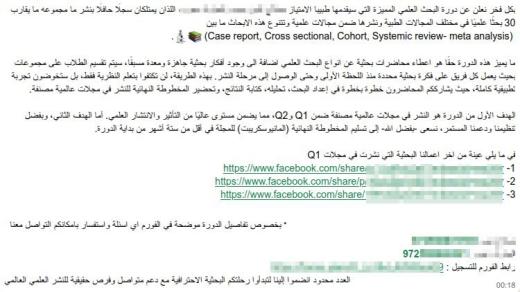
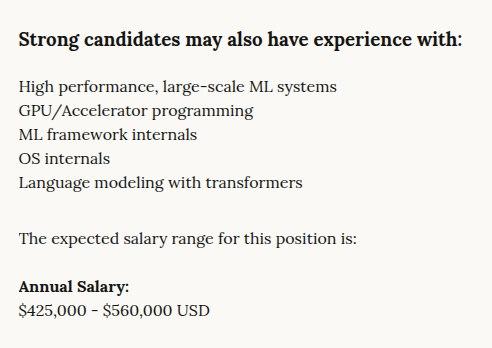
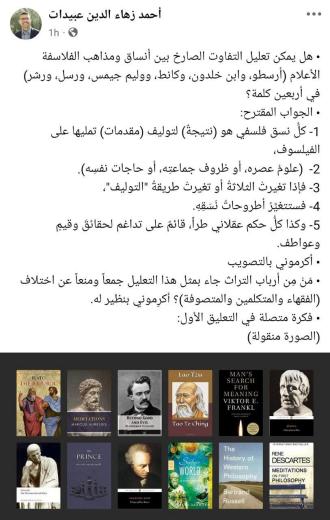
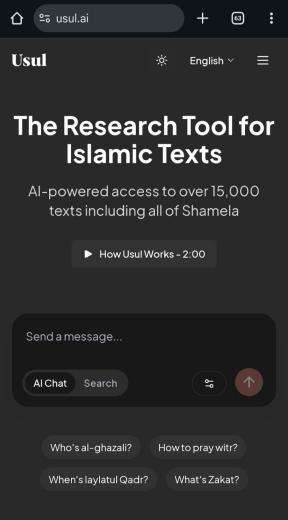
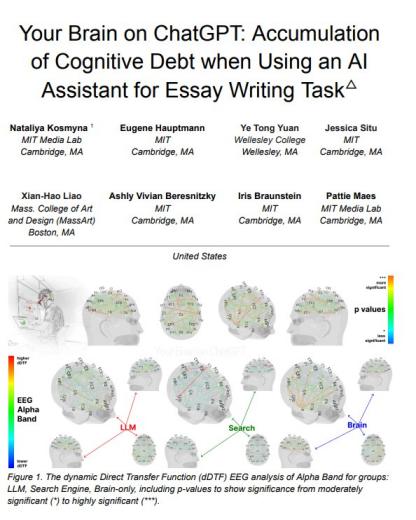
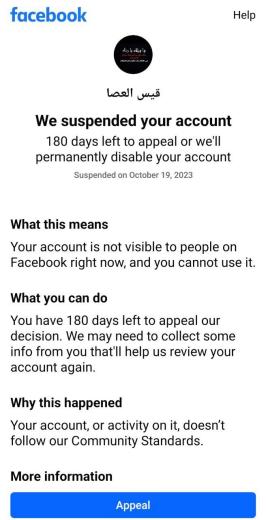
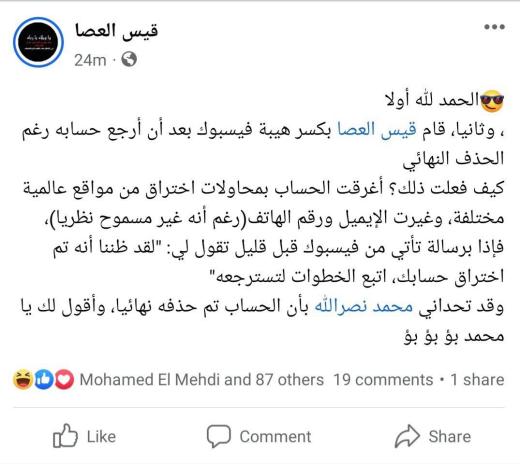
راح الحساب...
أرشيف كامل من قناة تيليغرام











































 01:08
01:08 








































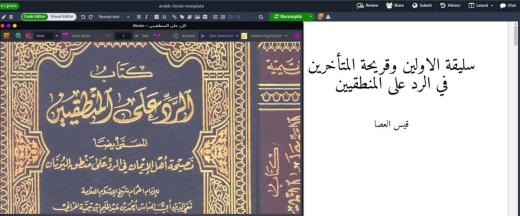

 00:09
00:09 


 00:22
00:22 







 01:17
01:17 



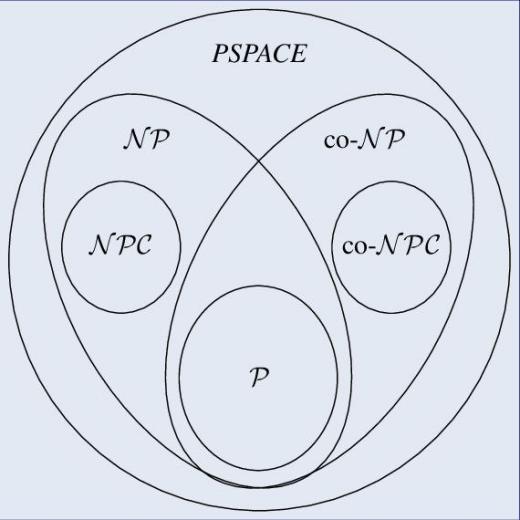


 00:20
00:20 
















































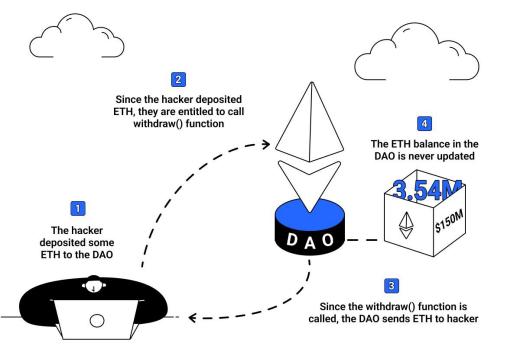

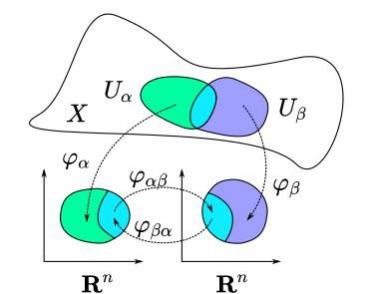



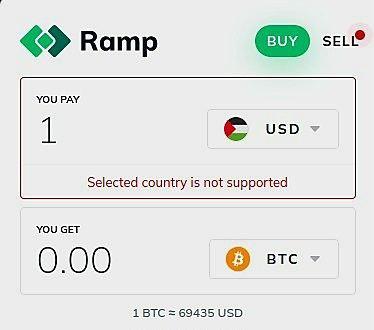
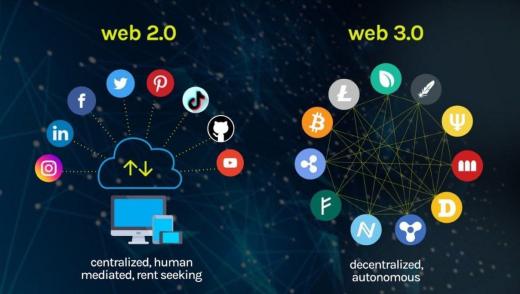

 01:04
01:04 








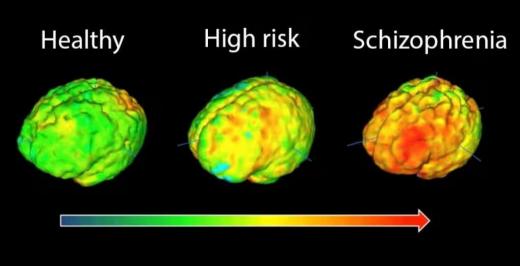



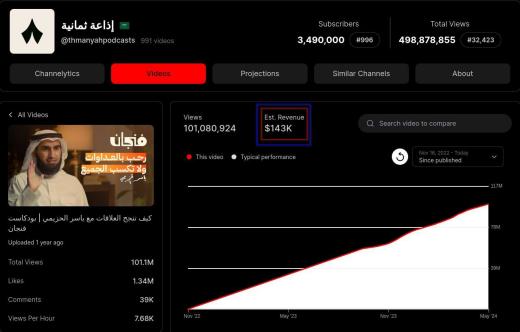




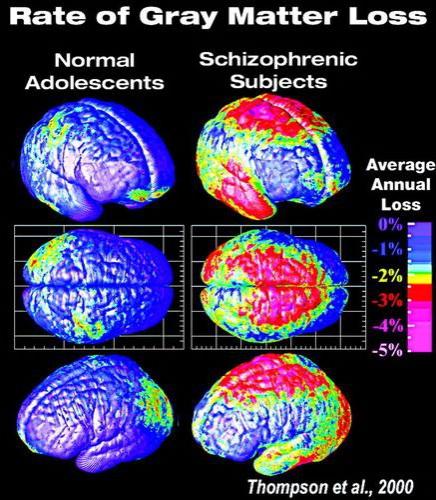

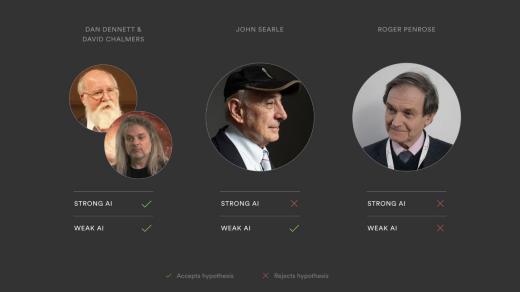





























 03:18
03:18 

 02:17
02:17 













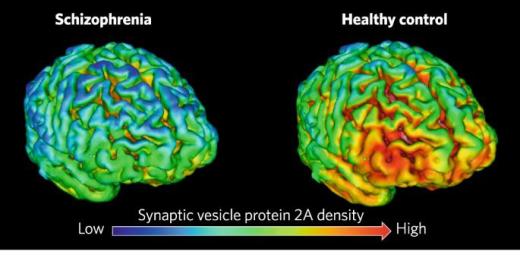



 11:50
11:50 






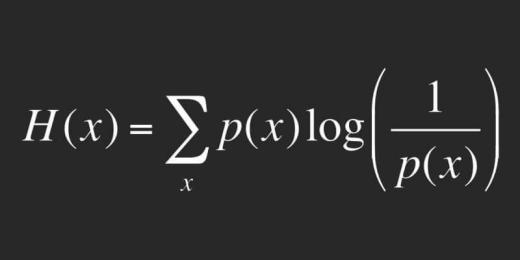



 00:39
00:39 

 00:33
00:33 

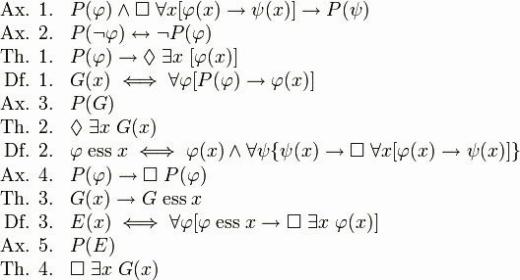






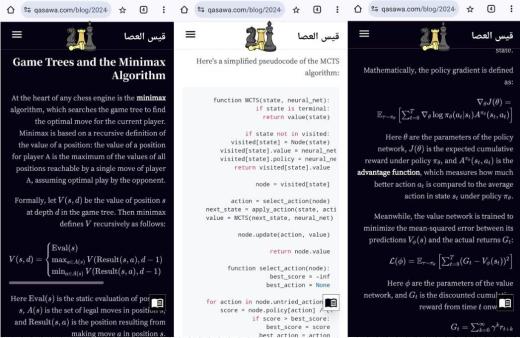


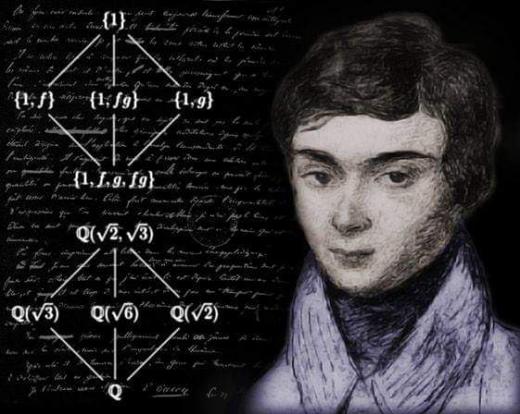

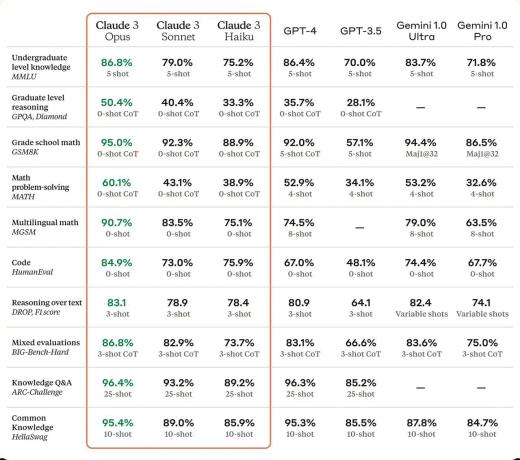












































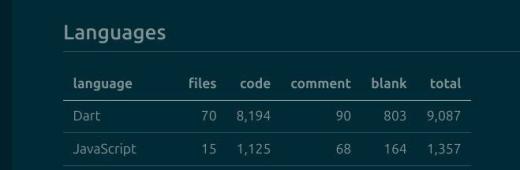

















 01:02
01:02 












 00:05
00:05 



 01:20
01:20 

.jpg)
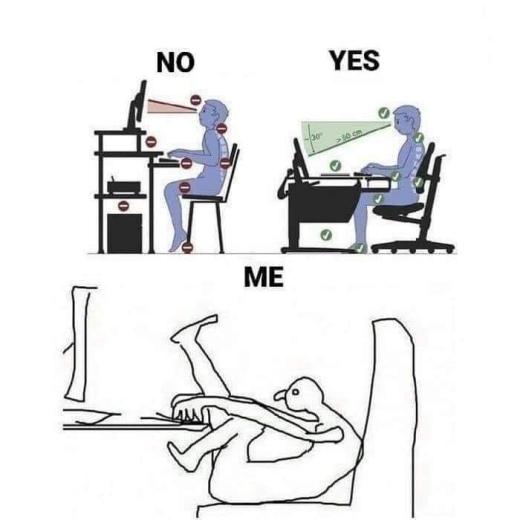




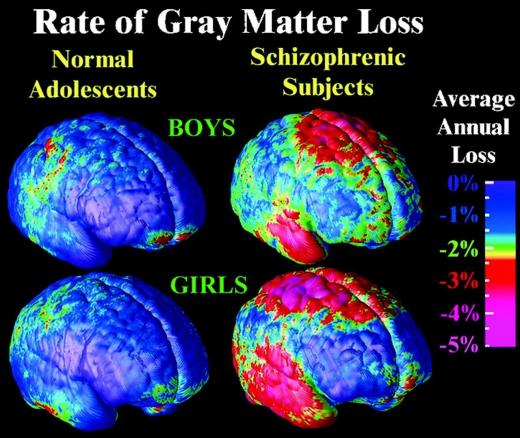
 00:14
00:14  00:26
00:26 




.jpg)

.jpg)
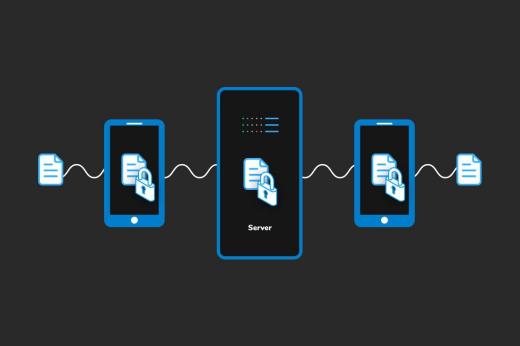
.jpg)









































 00:21
00:21 







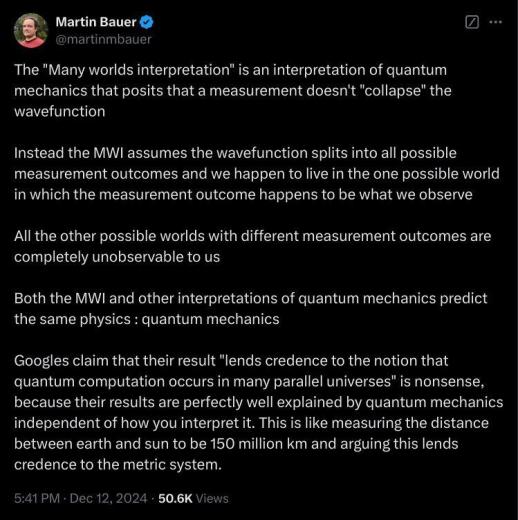


《فضرورةُ الكلام وورطةُ عدم وجودِ ما يقال وشهوةُ التَكَيُّس أمورٌ ثلاثة يُمكِنها أن تُحول أعظم رجل إلى مهزأة، وهم إذا كانوا راغيبن عن إيجاد أفكار جديدة فإنهم بحثوا عن لباقاتٍ جديدة فتكلموا بلا تفكير، كمنْ يعلُكُ بلا عِلْكٍ، وتظاهروا بالأكل مع خورهم جوعا》




 00:21
00:21 

 00:58
00:58 


.jpg)




.jpg)

.jpg)
 01:12
01:12 
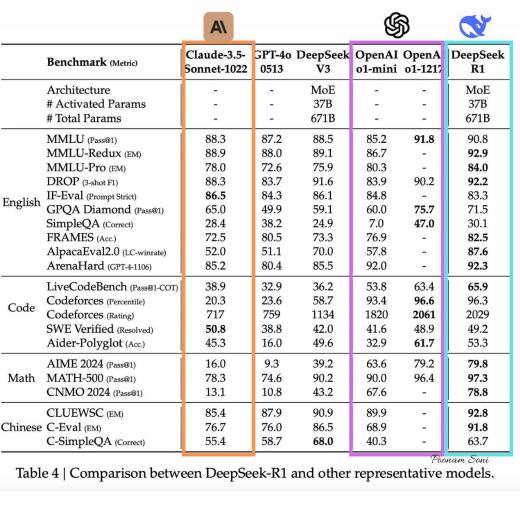













 03:28
03:28 







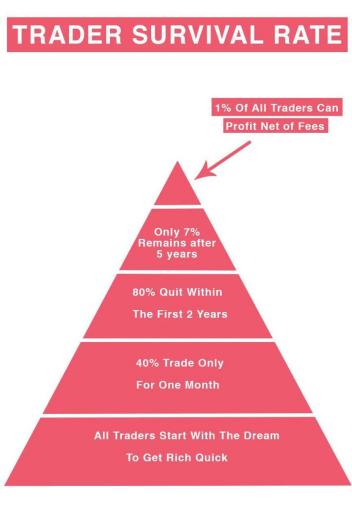
لا تكمن أهمية القضية في كونك مصيبا أو مخطئا، بل في كمية الأموال التي تجنيها حينما تكون مصيبا والكمية التي تخسرها حينما تكون مخطئا




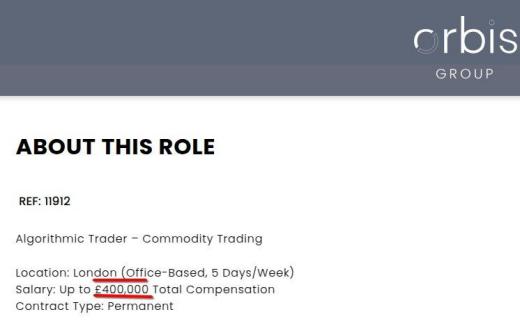
《إن كتابي الفلسفي الأول "مقالة في أسس الهندسة" —الذي كان تنقيحا لرسالة الزمالة— ليبدو لي الآن على شيء من السخف. فقد تناولت فيه سؤال كانط "كيف يمكن قيام علم للهندسة؟" وقررت أنه لا يكون ممكنا إلا إذا كان المكان نوعا من أنواع المكان الثلاثة المتعارف عليها: أولها إقليدي، والآخران لا إقليديان لكنهما يتصفان بأنهما يحتفظان "بمقياس ثابت للمنحنى Constant measure of Curvature". غير أن ثورة آينشتاين قد اكتسحت كل ما يمت بصلة لهذه الوجهة من النظر: فالهندسة في نظرية النسبية العامة لآينتشاين، هي من ذلك النوع الذي أعلنت [في كتابي] أنه مستحيل. وقد كان يمكن للنظرية الوترية Theory of Tensors التي أرسى عليها آينشتاين نظريته —أن تكون ذات عون في بحثي. لكنني لم أسمع بها قط إلا بعد أن استخدمها آينشتاين. لذلك لا أعتقد أن في ذلك الكتاب المبكر شيئا صحيحا، إذا ما استثنينا التفاصيل.》

.jpg)










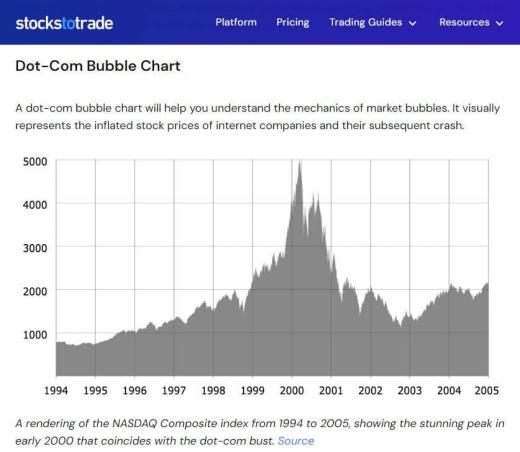

 00:19
00:19  00:10
00:10 



















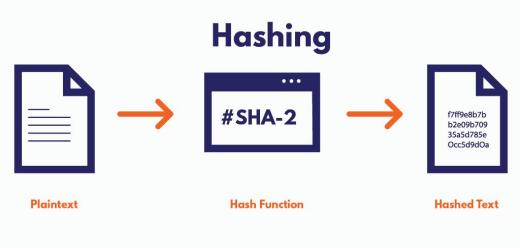
 00:05
00:05 








 02:57
02:57 
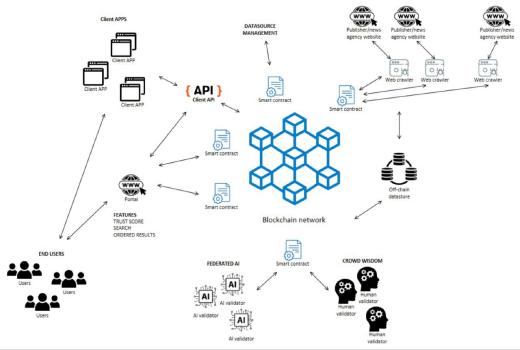






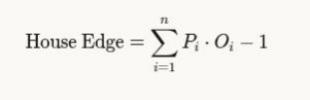

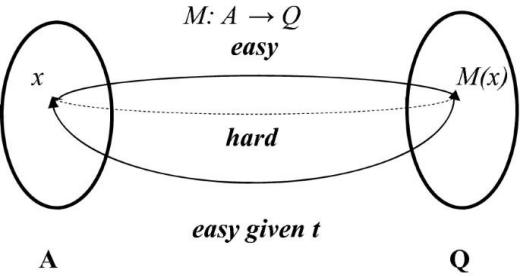


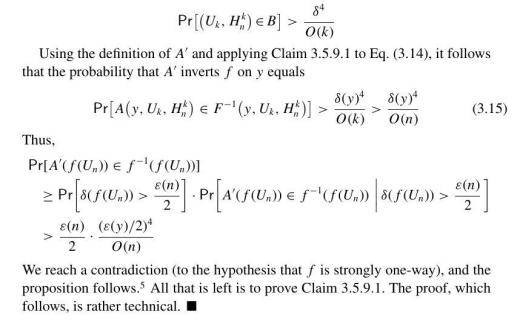



.jpg)




 05:23
05:23 




 00:49
00:49 



 00:13
00:13 
 00:41
00:41 


 00:25
00:25 

 00:54
00:54 

.jpg)


 00:07
00:07 
 00:23
00:23